Updated the latest Fortinet NSE4 exam questions and answers, pass the Fortinet NSE4 exam easily at first attempt with high quality Fortinet NSE4 dumps pdf training materials and study guides. https://www.leads4pass.com/nse4.html dumps pdf practice files. The best and most updated Security Expert NSE4 dumps exam training materials online free demo, download one of the many PDF readers that are available for free.
Download free latest Fortinet NSE4 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRaE1sNFV5ems4Tmc
Download free latest Microsoft MC1-001 dumps pdf files: https://drive.google.com/open?id=0B_7qiYkH83VRNFRJR0xPZm5oZUE
QUESTION 1
Two FortiGate units with NP6 processors form an active-active cluster. The cluster is doing security profile (UTM) inspection over all the user traffic . NSE4 pdf What statements are true regarding the sessions that the master unit is offloading to the slave unit for inspection? (Choose two.)
A. They are accelerated by hardware in the master unit.
B. They are not accelerated by hardware in the master unit.
C. They are accelerated by hardware in the slave unit.
D. They are not accelerated by hardware in the slave unit.
Correct Answer: AD
QUESTION 2
How do you configure a FortiGate to apply traffic shaping to P2P traffic , such as BitTorrent?
A. Apply a traffic shaper to a BitTorrent entry in an application control list, which is then applied to a firewall policy.
B. Enable the shape option in a firewall policy with service set to BitTorrent.
C. Define a DLP rule to match against BitTorrent traffic and include the rule in a DLP sensor with traffic shaping enabled.
D. Apply a traffic shaper to a protocol Options profile.
Correct Answer: A
QUESTION 3
Which of the following statements is correct regarding the FortiGuard Services Web Filtering Override
configuration as illustrated in the exhibit? NSE4 dumps
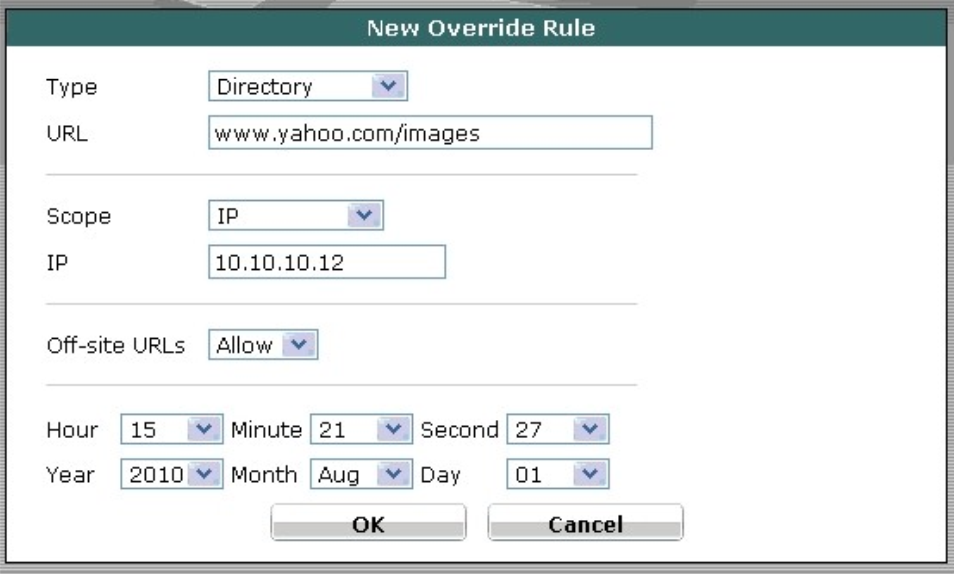
A. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/.
B. A client with an IP of address 10.10.10.12 is allowed access to any subdirectory that is part of the www.yahoo.com web site.
C. A client with an IP address of 10.10.10.12 is allowed access to the www.yahoo.com/images/ web site and any of its offsite URLs.
D. A client with an IP address of 10.10.10.12 is allowed access to any URL under the www.yahoo.com web site, including any subdirectory URLs, until August 7, 2009.
E. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/until August 7, 2009.
Correct Answer: C
QUESTION 4
Which of the following statements is correct about how the FortiGate unit verifies username and password during user authentication? NSE4 pdf
A. If a remote server is included in a user group, it will be checked before local accounts.
B. An administrator can define a local account for which the password must be verified by querying a remote server.
C. If authentication fails with a local password, the FortiGate unit will query the authentication server if the local user is configured with both a local password and an authentication server.
D. The FortiGate unit will only attempt to authenti ate against Action Directory if Fortinet Server Authentication Extensions are installed and configured.
Correct Answer: B
QUESTION 5
Which of the following statements is correct regarding the NAC Quarantine feature?
A. With NAC quarantine, files can be quarantined not only as a result of antivirus scanning, but also for other forms of content inspection such as IPS and DLP.
B. NAC quarantine does a client check on workstations before they are permitted to have administrative access to FortiGate.
C. NAC quarantine allows administrators to isolate clients whose network activity poses a security risk.
D. If you chose the quarantine action, you must decide whether the quarantine type is NAC quarantine or File quarantine.
Correct Answer: C
QUESTION 6
Which of the following statements is not correct regarding virtual domains (VDOMs)? NSE4 dumps
A. VDOMs divide a single FortiGate unit into two or more virtual units that function as multiple, independent units.
B. A management VDOM handles SNMP, logging, alert email, and FDN-based updates.
C. A backup management VDOM will synchronize the configuration from an active management VDOM.
D. VDOMs share firmware versions, as well as antivirus and IPS databases.
E. Only administrative users with a super_admin profile will be able to enter all VDOMs to make configuration changes.
Correct Answer: C
QUESTION 7
What advantages are there in using a hub-and-spoke IPSec VPN configuration instead of a fully-meshed set of IPSec tunnels? (Select all that apply.)
A. Using a hub and spoke topology is required to achieve full redundancy.
B. Using a hub and spoke topology simplifies configuration because fewer tunnels are required.
C. Using a hub and spoke topology provides stronger encryption.
D. The routing at a spoke is simpler, compared to a meshed node.
Correct Answer: BD
QUESTION 8
Which of the following Session TTL values will take precedence?
A. Session TTL specified at the system level for that port number
B. Session TTL specified in the matching firewall policy
C. Session TTL dictated by the application control list associated with the matching firewall policy
D. The default session TTL specified at the system level
Correct Answer: C
QUESTION 9
Which of the following statements are correct about the HA diag command diagnose sys ha reset-uptime? (Select all that apply.)
A. The device this command is executed on is likely to switch from master to slave status if master override is disabled.
B. The device this command is executed on is likely to switch from master to slave status if master override is enabled.
C. This command has no impact on the HA algorithm.
D. This command resets the uptime variable used in the HA algorithm so it may cause a new master to become elected.
Correct Answer: AD
QUESTION 10
The FortiGate unit can be configured to allow authentication to a RADIUS server. The RADIUS server can use several different authentication protocols during the authentication process. NSE4 dumps Which of the following are valid authentication protocols that can be used when a user authenticates to the RADIUS server? (Select all that apply.)
A. MS-CHAP-V2 (Microsoft Challenge-Handshake Authentication Protocol v2)
B. PAP (Password Authentication Protocol)
C. CHAP (Challenge-Handshake Authentication Protocol)
D. MS-CHAP (Microsoft Challenge-Handshake Authentication Protocol v1)
E. FAP (FortiGate Authentication Protocol)
Correct Answer: ABCD
Read more: https://www.leads4pass.com/nse4.html dumps exam questions and answers.