
New 312-50V12 dumps contain 528 latest exam questions and answers are the best material to prepare for the CEHv12 certification exam!
New 312-50V12 dumps are edited and corrected by the EC-COUNCIL expert team, participating in real scenarios to verify that it is true and effective, which can ensure 100% success in passing the CEHv12 certification exam.
Download New 312-50V12 dumps: https://www.pass4itsure.com/312-50v12.html, use PDF or VCE tools to help you learn easily, and prepare for the CEHv12 certification exam preparation.
Share some New 312-50V12 dumps exam questions online practice:
| From | Number of exam questions | Prep Exam |
| Pass4itsure | 15 | 312-50v12 |
Question 1:
To create a botnet. the attacker can use several techniques to scan vulnerable machines. The attacker first collects Information about a large number of vulnerable machines to create a list. Subsequently, they infect the machines. The list Is divided by assigning half of the list to the newly compromised machines. The scanning process runs simultaneously. This technique ensures the spreading and installation of malicious code in little time.
Which technique is discussed here?
A. Hit-list-scanning technique
B. Topological scanning technique
C. Subnet scanning technique
D. Permutation scanning technique
Correct Answer: A
One of the biggest problems a worm faces in achieving a very fast rate of infection is “getting off the ground.” although a worm spreads exponentially throughout the early stages of infection, the time needed to infect say the first 10,000 hosts dominates the infection time. There is a straightforward way for an active worm a simple obstacle, that we term hit-list scanning.
Before the worm is free, the worm author collects a listing of say ten,000 to 50,000 potentially vulnerable machines, ideally ones with sensible network connections.
The worm, when released onto an initial machine on this hit list, begins scanning down the list. once it infects a machine, it divides the hit list in half, communicating half to the recipient worm, and keeping the other half.
This fast division ensures that even if only 10-20% of the machines on the hit list are actually vulnerable, an active worm can quickly bear the hit list and establish itself on all vulnerable machines in only some seconds. though the hit list could begin at 200 kilobytes, it quickly shrinks to nothing during the partitioning.
This provides a great benefit in constructing a quick worm by speeding up the initial infection. The hit list needn’t be perfect: a simple list of machines running a selected server sort could serve, though larger accuracy can improve the unfold.
The hit list itself is generated victimization one or many of the following techniques, ready well before, typically with very little concern of detection. Stealthy scans. Portscans are so common and then widely ignored that even a quick scan of the whole network would be unlikely to attract law enforcement attention or gentle comment within the incident response community.
However, for attackers who wish to be particularly careful, a randomized sneaky scan taking many months would be not possible to attract much attention, as most intrusion detection systems are not currently capable of detecting such low-profile scans.
Some portion of the scan would be out of date by the time it had been used, however abundant of it\’d not. Distributed scanning. an assailant might scan the web using a few dozen to some thousand already-compromised “zombies,” the same as what DDOS attackers assemble in a very fairly routine fashion.
Such distributed scanning has already been seen within the Lawrence Berkeley National Laboratory received ten throughout the past year. DNS searches. Assemble a list of domains (for example, by using widely offered spam mail lists, or trolling the address registries).
The DNS will then be searched for the science addresses of mail servers (via mx records) or net servers (by looking for www.domain.com). Spiders. Net server worms (like Code Red), use Web-crawling techniques the same as search engines so as to produce a list of most Internet-connected websites. this would be unlikely to draw serious attention.
Public surveys. for many potential targets, there may be surveys available listing them, like the Netcraft survey. Just listen. Some applications, like peer-to-peer networks, wind up advertising many of their servers.
Similarly, many previous worms effectively broadcast that the infected machine is vulnerable to further attack. easy, because of its widespread scanning, during the Code Red I infection it was easy to select the addresses of upwards of 300,000 vulnerable IIS servers because each came knocking on everyone\’s door!
Question 2:
Every company needs a formal written document that spells out to employees precisely what they are allowed to use the company\’s systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization.
The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company\’s computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
A. Information Audit Policy (IAP)
B. Information Security Policy (ISP)
C. Penetration Testing Policy (PTP)
D. Company Compliance Policy (CCP)
Correct Answer: B
Question 3:
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
A. Network elements must be hardened with user ids and strong passwords. Regular security tests and audits should be performed.
B. As long as physical access to the network elements is restricted, there is no need for additional measures.
C. There is no need for specific security measures on the network elements as long as firewalls and IPS systems exist.
D. The operator knows that attacks and downtime are inevitable and should have a backup site.
Correct Answer: A
Question 4:
In Trojan terminology, what is a covert channel?

A. A channel that transfers information within a computer system or network in a way that violates the security policy
B. A legitimate communication path within a computer system or network for transfer of data
C. It is a kernel operation that hides boot processes and services to mask detection
D. It is a Reverse tunneling technique that uses HTTPS protocol instead of HTTP protocol to establish connections
Correct Answer: A
Question 5:
Richard, an attacker, targets an MNC. In this process, he uses a footprinting technique to gather as much information as possible. Using this technique, he gathers domain information such as the target domain name, contact details of its owner, expiry date, and creation date. With this information, he creates a map of the organization\’s network and misleads domain owners with social engineering to obtain internal details of its network. What type of footprinting technique is employed by Richard?
A. VoIP footprinting
B. VPN footprinting
C. Whois footprinting
D. Email footprinting
Correct Answer: D
Question 6:
What is not a PCI compliance recommendation?
A. Use a firewall between the public network and the payment card data.
B. Use encryption to protect all transmission of cardholder data over any public network.
C. Rotate employees handling credit card transactions on a yearly basis to different departments.
D. Limit access to cardholder data to as few individuals as possible.
Correct Answer: C
https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security Build and Maintain a Secure Network
1.
Install and maintain a firewall configuration to protect cardholder data.
2.
Do not use vendor-supplied defaults for system passwords and other security parameters. Protect Cardholder Data
3.
Protect stored cardholder data.
4.
Encrypt transmission of cardholder data across open, public networks. Maintain a Vulnerability Management Program
5.
Use and regularly update anti-virus software or programs.
6.
Develop and maintain secure systems and applications. Implement Strong Access Control Measures
7.
Restrict access to cardholder data by business need-to-know.
8.
Assign a unique ID to each person with computer access.
9.
Restrict physical access to cardholder data. Regularly Monitor and Test Networks
10.
Track and monitor all access to network resources and cardholder data.
11.
Regularly test security systems and processes. Maintain an Information Security Policy
12.
Maintain a policy that addresses information security for employees and contractors.
Question 7:
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool “SIDExtractor”. Here is the output of the SIDs:
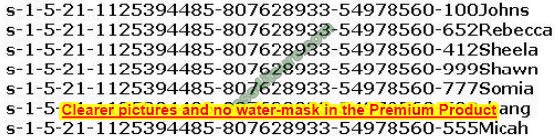
From the above list identify the user account with System Administrator privileges.
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah
Correct Answer: F
Question 8:
An organization decided to harden its security against web application and web-server attacks. John, the security personnel in the organization, employed a security scanner to automate web-application security testing and to guard the organization\’s web infrastructure against web application threats. Using that tool, he also wants to detect XSS, directory transversal problems, fault injection, SQL injection, attempts to execute commands, and several other attacks. Which of the following security scanners will help John perform the above task?
A. AlienVault OSSIM
B. Syhunt Hybrid
C. Saleae Logic Analyzer
D. Cisco ASA
Correct Answer: B
Question 9:
What did the following commands determine?
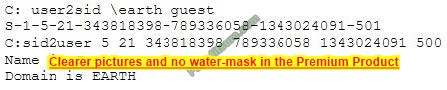
A. That the Joe account has a SID of 500
B. These commands demonstrate that the guest account has NOT been disabled
C. These commands demonstrate that the guest account has been disabled
D. That the true administrator is Joe
E. Issued alone, these commands prove nothing
Correct Answer: D
Question 10:
Wilson, a professional hacker, targets an organization for financial benefit and plans to compromise its systems by sending malicious emails. For this purpose, he uses a tool to track the emails of the target and extracts information such as sender identities, mall servers, sender IP addresses, and sender locations from different public sources. He also checks if an email address was leaked using the haveibeenpwned.com API. Which of the following tools is used by Wilson in the above scenario?
A. Factiva
B. Netcraft
C. info gap
D. Zoominfo
Correct Answer: C
Infoga may be a tool gathering email account information (ip, hostname, country,…) from completely different public supply (search engines, pgp key servers, and Shodan) and checking if the email was leaked using haveibeenpwned.com API. is a really simple tool, however very effective for the first stages of a penetration test or just to know the visibility of your company within the net.
Question 11:
In this attack, a victim receives an e-mail claiming from PayPal stating that their account has been disabled and confirmation is required before activation. The attackers then scam to collect not one but two credit card numbers, ATM PIN numbers, and other personal details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect and related to this attack?
A. Do not reply to email messages or popup ads asking for personal or financial information
B. Do not trust telephone numbers in e-mails or popup ads
C. Review credit card and bank account statements regularly
D. Antivirus, anti-spyware, and firewall software can very easily detect these types of attacks
E. Do not send credit card numbers, and personal or financial information via e-mail
Correct Answer: D
Question 12:
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack.
You also notice “/bin/sh” in the ASCII part of the output.
As an analyst what would you conclude about the attack?

A. The buffer overflow attack has been neutralized by the IDS
B. The attacker is creating a directory on the compromised machine
C. The attacker is attempting a buffer overflow attack and has succeeded
D. The attacker is attempting an exploit that launches a command-line shell
Correct Answer: D
Question 13:
which of the following information security controls creates an appealing isolated environment for hackers to prevent them from compromising critical targets while simultaneously gathering information about the hacker?
A. intrusion detection system
B. Honeypot
C. Botnet
D. Firewall
Correct Answer: B
A honeypot may be a trap that an IT pro lays for a malicious hacker, hoping that they will interact with it in a way that gives useful intelligence. It\’s one of the oldest security measures in IT, but beware: luring hackers onto your network, even on an isolated system, is often a dangerous game. honeypot may be a good starting place: “A honeypot may be a computer or computing system intended to mimic likely targets of cyberattacks.”
Often a honeypot is going to be deliberately configured with known vulnerabilities in a situation to form a more tempting or obvious target for attackers.
A honeypot won’t contain production data or participate in legitimate traffic on your network — that\’s how you\’ll tell anything happening within it\’s a result of an attack. If someone\’s stopping by, they\’re up to no good.
That definition covers a various array of systems, from bare-bones virtual machines that only offer a couple of vulnerable systems to ornately constructed fake networks spanning multiple servers. and therefore the goals of those who build honeypots can vary widely also, starting from defense thorough to academic research. additionally, there\’s now an entire marketing category of deception technology that, while not meeting the strict definition of a honeypot, is certainly within the same family.
But we\’ll get thereto during a moment. honeypots aim to permit close analysis of how hackers do their dirty work. The team controlling the honeypot can watch the techniques hackers use to infiltrate systems, escalate privileges, and otherwise run amok through target networks.
These sorts of honeypots are found by security companies, academics, and government agencies looking to look at the threat landscape.
Their creators could also be curious about learning what kind of attacks are out there, getting details on how specific sorts of attacks work, or maybe trying to lure specific hackers in the hopes of tracing the attack back to its source.
These systems are often inbuilt in fully isolated lab environments, which ensures that any breaches don’t end in non-honeypot machines falling prey to attacks.
Production honeypots, on the opposite hand, are usually deployed in proximity to some organization\’s production infrastructure, though measures are taken to isolate it in the maximum amount possible.
These honeypots often serve both as bait to distract hackers who could also be trying to interrupt that organization\’s network, keeping them far away from valuable data or services; they will also function as a canary within the coalpit, indicating that attacks are underway and are a minimum of partially succeeding.
Question 14:
What is the role of test automation in security testing?
A. It is an option but it tends to be very expensive.
B. It should be used exclusively. Manual testing is outdated because of low speed and possible test setup inconsistencies.
C. Test automation is not usable in security due to the complexity of the tests.
D. It can accelerate benchmark tests and repeat them with a consistent test setup. But it cannot replace manual testing completely.
Correct Answer: D
Question 15:
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
A. JSON-RPC
B. SOAP API
C. RESTful API
D. REST API
Correct Answer: C
*REST is not a specification, tool, or framework, but instead is an architectural style for web services that serve as a communication medium between various systems on the web. *RESTful APIs, which are also known as RESTful services, are designed using REST principles and HTTP communication protocols RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE
RESTful API: RESTful API is a RESTful service that is designed using REST principles and HTTP communication protocols. RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE. RESTful API is also designed to make applications independent to improve the overall performance, visibility, scalability, reliability, and portability of an application.
APIs with the following features can be referred to as RESTful APIs: o Stateless: The client end stores the state of the session; the server is restricted to save data during the request processing o Cacheable: The client should save responses (representations) in the cache. This feature can enhance API performance pg. 1920 CEHv11 manual.
https://cloud.google.com/files/apigee/apigee-web-api-design-the-missing-link-ebook.pdf
The HTTP methods GET, POST, PUT or PATCH, and DELETE can be used with these templates to read, create, update, and delete description resources for dogs and their owners.
This API style has become popular for many reasons. It is straightforward and intuitive, and learning this pattern is similar to learning a programming language API. APIs like this one are commonly called RESTful APIs, although they do not display all of the characteristics that define REST (more on REST later).
…
New 312-50V12 dumps are the best exam material for your exam preparation, you only need 3-5 days of practice preparation to help you pass the CEHv12 certification exam!
Download New 312-50V12 dumps: https://www.pass4itsure.com/312-50v12.html, use PDF or VCE tools to help you learn easily! Guarantee that you will pass the CEHv12 certification exam 100% successfully.